
Is Your Data Held Hostage? There’s A Ransomware Negotiator For That
Cyber attacks, usually involving ransomware, are being perpetrated against corporations and state-owned agencies every day. ~Mark Lance, Guidepoint Security
Chris Summers | The Epoch Times
Mark Lance’s phone rings when a company’s data is being held hostage. Often, the perpetrators are demanding a ransom to return sensitive information.
“The largest demand for one of our victims was $70 million,” said Lance, a ransomware negotiator with Virginia-based Guidepoint Security.
 Mark Lance, Courtesy of Guidepoint Security
Mark Lance, Courtesy of Guidepoint Security
“The largest demand for one of our victims was $70 million,” said Lance, a ransomware negotiator with Virginia-based Guidepoint Security.
Failure to pay is under the threat that the company’s information will be made public.
“The earlier we get engaged, the better,” Lance told The Epoch Times.
“In most circumstances … a client has already recognized that they’ve been a victim—they’ve been informed via ransom notes,” he said.
“We help people recognize that even if there’s no intent on paying a ransom, there’s a tremendous amount of value in engaging the cyber criminals, because … you can still do things like delay the inevitable release of their information, which will allow for more time for the forensics and incident response work stream to make sure that they are patched.”
Cyber attacks, usually involving ransomware, are being perpetrated against corporations and state-owned agencies in the United States every day.
In the first half of 2025, a Comparitech report shows 208 ransomware attacks on government agencies globally, a 65 percent increase from the same period of 2024.
Ransomware is a type of malicious software—or malware—that prevents a user from accessing his or her computer files, systems, or networks and demands that he or she pay a ransom for their return, according to the FBI.
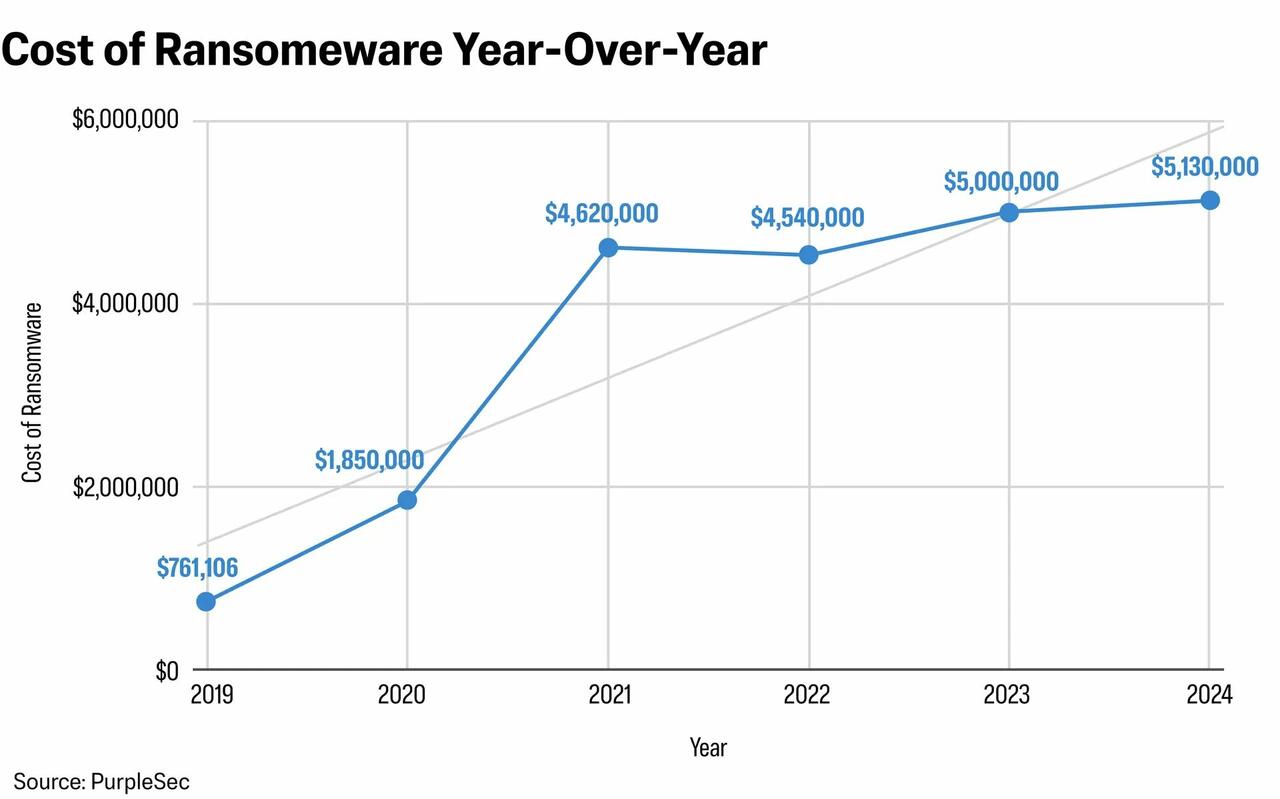
The average cost to the victim of a ransomware attack has risen from $761,106 in 2019 to an estimated $5.13 million in 2025, according toPurpleSec, a U.S.-based cybersecurity company.
That includes the ransom payment itself, the recovery costs, and various indirect costs such as reputational damage.
Lance, who has worked in cybersecurity for 25 years, said when he is called in at the early stage of an attack, the victim is usually still performing a business impact analysis.
“They’re not necessarily sure what has fully transpired or has occurred within their environment, to know what they potentially need to do as next steps,” he said.
By “environment,” Lance means all the hardware, software, and networks that support an organization’s operating systems.
He said a ransomware negotiator can manage expectations and give the victim an idea of their options.
He said he can buy valuable time, and also allow the victim to work with legal counsel to determine what sort of disclosure they are going to have to make to the public, to stockholders, to the Securities and Exchange Commission (SEC), and other regulators.
Lance said the threat actors also have to provide some sort of evidence that they have accessed the victim’s data, and will have to provide a file tree, which is a map of directories leading to the files they have accessed.
“We can gather and glean information from those communications that can be shared, that they might not have otherwise. But yeah, the earlier [we are brought in], the better,” he said.
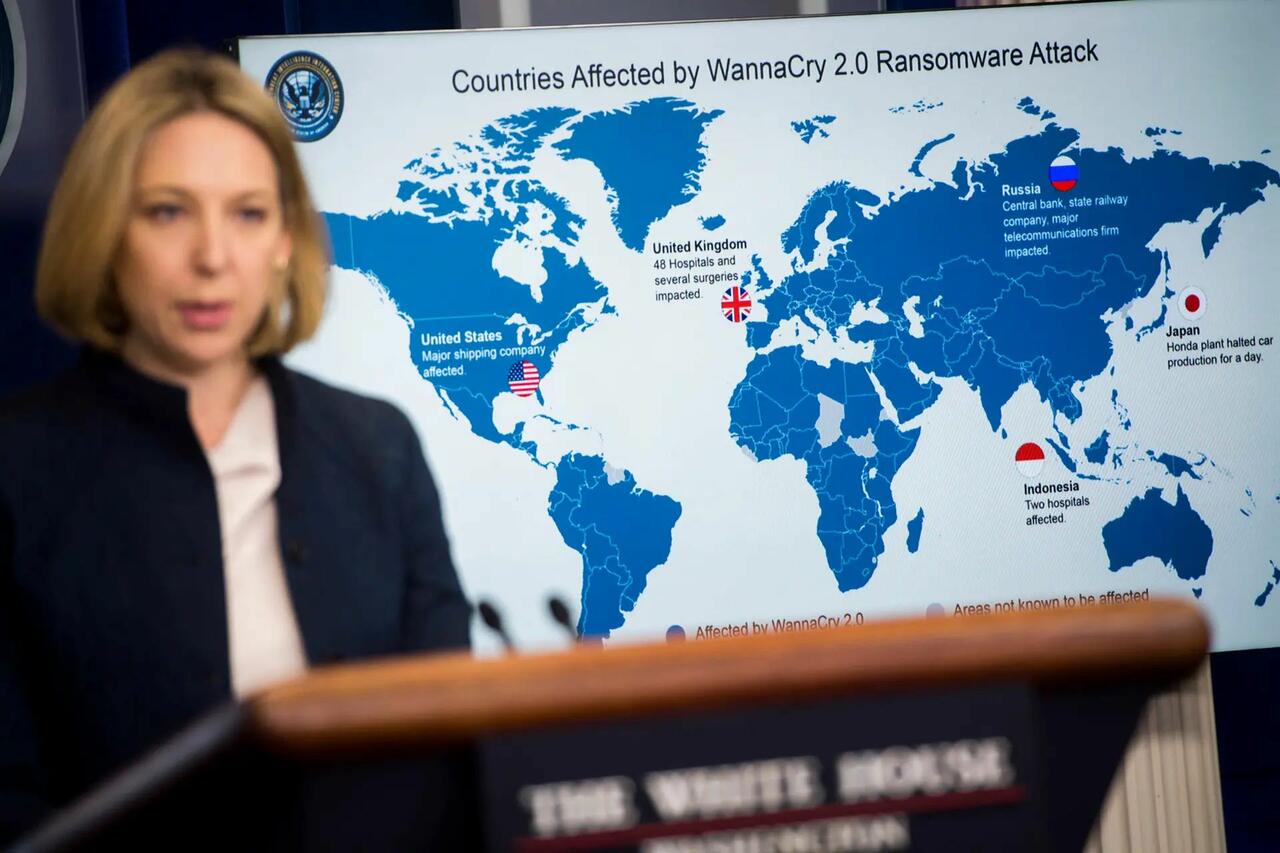 Jeanette Manfra, chief cybersecurity official for the Department of Homeland Security, speaks during a briefing at the White House on Dec. 19, 2017. Manfra announced that the United States believes North Korea was behind the global WannaCry cyberattacks. Saul Loeb/AFP via Getty Images
Jeanette Manfra, chief cybersecurity official for the Department of Homeland Security, speaks during a briefing at the White House on Dec. 19, 2017. Manfra announced that the United States believes North Korea was behind the global WannaCry cyberattacks. Saul Loeb/AFP via Getty Images
Lance said at an early stage he tries to figure out what the client wants from the communication with the ransomware gang, “and then we develop a strategy around that.”
He said the initial strategy might be simply to delay while they find out more about the attack and how serious it is in terms of consequences.
He said the victim might later decide they are willing to make a ransom payment, and he said, “Then our strategy changes into how we’re negotiating terms, like, do they need it quickly? Or do we have time? So our strategy will change based on the needs of the client and what they’re trying to get out of it.”
Cyber Ransom Notes
Most often, the ransom note is left as a message on an individual system, Lance said. The note will usually advise the victim not to try to touch any of the IT systems and to download a Tor browser, go to a website on the darknet, and initiate communications with the ransomware attackers.
Read the rest here…
Header featured image (edited) credit: dpa/picture-alliance, Annette Riedl. Emphasis added by (TLB)
••••
••••
Stay tuned…
![]()
••••
The Liberty Beacon Project is now expanding at a near exponential rate, and for this we are grateful and excited! But we must also be practical. For 7 years we have not asked for any donations, and have built this project with our own funds as we grew. We are now experiencing ever increasing growing pains due to the large number of websites and projects we represent. So we have just installed donation buttons on our websites and ask that you consider this when you visit them. Nothing is too small. We thank you for all your support and your considerations … (TLB)
••••
Comment Policy: As a privately owned web site, we reserve the right to remove comments that contain spam, advertising, vulgarity, threats of violence, racism, or personal/abusive attacks on other users. This also applies to trolling, the use of more than one alias, or just intentional mischief. Enforcement of this policy is at the discretion of this websites administrators. Repeat offenders may be blocked or permanently banned without prior warning.
••••
Disclaimer: TLB websites contain copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available to our readers under the provisions of “fair use” in an effort to advance a better understanding of political, health, economic and social issues. The material on this site is distributed without profit to those who have expressed a prior interest in receiving it for research and educational purposes. If you wish to use copyrighted material for purposes other than “fair use” you must request permission from the copyright owner.
••••
Disclaimer: The information and opinions shared are for informational purposes only including, but not limited to, text, graphics, images and other material are not intended as medical advice or instruction. Nothing mentioned is intended to be a substitute for professional medical advice, diagnosis or treatment.

Leave a Reply